Introduction
As Secure Cloud Data Center becomes the standard infrastructure for virtualized server deployments, Rimici “ONE Source” has consolidate servers that belong to different trust zones. A trust zone is loosely defined as a network segment within which data flows relatively freely, whereas data flowing in and out of the trust zone is subject to stronger restrictions. Examples of trust zones include:- Demilitarized zones (DMZs)
- Payment card industry (PCI) cardholder data environment
- Site-specific zones, such as segmentation according to department or function
- Application-defined zones, such as the three tiers of a Web Application
- Rimici Private Cloud Security Operations Center
- Harden and isolate the service console and management network
- Enforce consistency of network configuration across all hosts
- Set Layer 2 security options on cloud switches
- Enforce separation of duties
- Use Rimici cloud resource management capabilities
- Regularly audit virtualized configuration
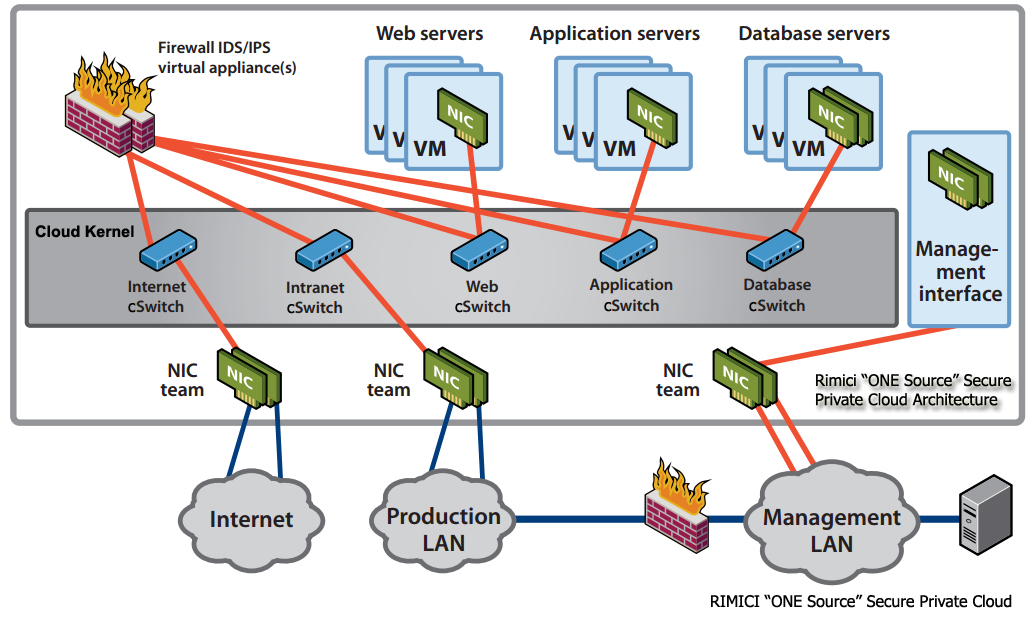
Rimici “ONE Source” Secure Cloud Best Practices for Achieving a Secure Virtualized Mixed Trust Zone Deployment
Most security issues do not arise from the cloud virtualization infrastructure itself but from cloud administrative and operational challenges. The primary risks are caused by a loss of separation of duties. When this occurs, individuals who lack the necessary experience and capabilities are given an opportunity to introduce vulnerabilities through misconfiguration. For instance, they can accidentally place the virtual NIC of a virtual machine in the wrong trust zone.
This risk — which also can also occur in purely physical environments — can breach the isolation between networks and virtual machines of different trust levels. Rimici “ONE Source” Secure Cloud Data Center and infrastructure is designed by a team of secure cloud senior architectures, administrators and security operations center experts from Silicon Valley. The architecture is built with resiliency, high availability, scalability and elastic network, storage and operations. We ensured that the Rimici “ONE Source” Secure cloud is built from the ground up to implement and meet ISO 27002. We have then implemented ISO 27001 Cloud Information Security Management System to manage the cloud security operations and risk management meeting privacy and security requirements.
Harden and Isolate the Service Console and Management Network
This step is especially important because access to the service console of an RIMICI “ONE SOURCE” secure cloud host gives a user with root privileges full control over the virtual machines on that host. Although access to the service console is secured through authentication, you can provide additional security against unauthorized access by creating additional layers of security.
In addition, you should isolate the service console. To do so, make sure that the network to which the service console is isolated is firewalled and accessible only to authorized administrators.
You can use a VPN or other access control methods to restrict access to the management network.
Enforce Consistency of Network Configuration Across All Hosts
Ensuring that the virtual network is configured in a consistent manner across all hosts is particularly critical because accidentally connecting virtual servers to the wrong networks can undermine all other security efforts. By clearly labeling the networks, you make it less likely that a virtual machine can be connected to an unauthorized network accidentally.
Set Layer 2 Security Options on Virtual Switches
Protect against attacks such as data snooping, sniffing, and MAC spoofing by disabling the promiscuous mode, MAC address changes, and forged transmissions capabilities on the virtual network interfaces. These capabilities are very rarely needed and create opportunities for exploitation.
Fortunately, in the VMware virtual network layer you have full control over these options, something that is not the case in purely physical environments.
Enforce Separation of Duties
Mitigate configuration mistakes by using cloud operations Center to define roles and responsibilities for each administrator of the vSphere infrastructure. By distributing rights based on skills and responsibilities, you can significantly reduce the chance of misconfiguration.
As an added benefit, this method also limits the amount of authority any one administrator has over the system as a whole. In particular, you should restrict privileges for performing the following actions:
- Reconfiguring virtual networks
- Assigning virtual machines to sensitive networks
- Changing firewall or other network security policies
Use Rimici Secure Cloud Resource Management Capabilities
Denial of service within a virtual environment can occur if an individual virtual machine is allowed to use a disproportionate share of RIMICI “ONE SOURCE” secure cloud host resources. In so doing, it starves other virtual machines running on the same RIMICI “ONE SOURCE” secure cloud host. Such denial of service can occur as the result of malicious intent or accidentally, but you can guard against this possibility by setting resource reservations and limits for virtual machines using cloud operations Center. You should use the same resource controls to ensure that sufficient resources are available to virtual network security devices.
Regularly Audit the Virtualized Configuration
Regular audit of configurations is essential in both physical and virtual environments. When virtualizing any part of your infrastructure, it is important to audit the configurations of all of the components — including cloud operations Center, cloud Switches, virtual and physical firewalls, and any other security devices —regularly. You must conduct these audits to make sure that changes to configurations can be controlled and that the changes do not cause a security hole in the configuration. The use of configuration management and compliance tools can greatly assist with the audit process. Audits are especially important for the second and third options discussed in this paper because the risk of misconfiguration is much higher in those topologies.
Conclusion
Our families and businesses can take advantage of the benefits of Rimici “ONE Source” secure cloud data center and resources in setting up mixed trust zones, and we can do so securely, maintaining compliance with our organization’s policies. There are a number of configurations you can use to achieve this goal.
















